Introducing Google’s online security efforts
May 21st, 2007 | Published in Google Online Security
Online security is an important topic for Google, our users, and anyone who uses the Internet. The related issues are complex and dynamic and we've been looking for a way to foster discussion on the topic and keep users informed. Thus, we've started this blog where we hope to periodically provide updates on recent trends, interesting findings, and efforts related to online security. Among the issues we'll tackle is malware, which is the subject of our inaugural post.
Malware -- surreptitious software capable of stealing sensitive information from your computer -- is increasingly spreading over the web. Visiting a compromised web server with a vulnerable browser or plugins can result in your system being infected with a whole variety of malware without any interaction on your part. Software installations that leverage exploits are termed "drive-by downloads". To protect Google's users from this threat, we started an anti-malware effort about a year ago. As a result, we can warn you in our search results if we know of a site to be harmful and even prevent exploits from loading with Google Desktop Search.
Unfortunately, the scope of the problem has recently been somewhat misreported to suggest that one in 10 websites are potentially malicious. To clarify, a sample-based analysis puts the fraction of malicious pages at roughly 0.1%. The analysis described in our paper covers billions of URLs. Using targeted feature extraction and classification, we select a subset of URLs believed to be suspicious for in-depth investigation. So far, we have investigated about 12 million suspicious URLs and found about 1 million that engage in drive-by downloads. In most cases, the web sites that infect your system with malware are not intentionally doing so and are often unaware that their web servers have been compromised.
To get a better understanding about the geographic distribution of sites engaging in drive-by downloads, we analyzed the location of compromised web sites and the location of malware distribution hosts. At the moment, the majority of malware activity seems to happen in China, the U.S., Germany and Russia (see below):
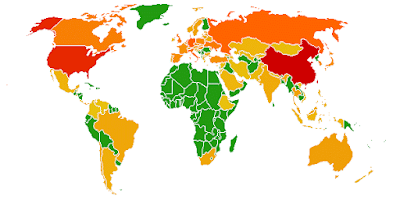 Location of compromised web sites. These are often sites that are benign in nature but have been compromised and have become dangerous for users to visit.
Location of compromised web sites. These are often sites that are benign in nature but have been compromised and have become dangerous for users to visit.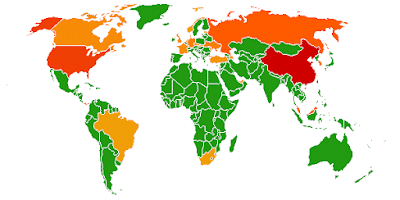 Location of malware distribution servers. These are servers that are used by malware authors to distribute their payload. Very often the compromised sites are modified to include content from these servers. The color coding works as follows: Green means that we did not find anything unsual in that country, yellow means low activity, orange medium activity and red high activity.
Location of malware distribution servers. These are servers that are used by malware authors to distribute their payload. Very often the compromised sites are modified to include content from these servers. The color coding works as follows: Green means that we did not find anything unsual in that country, yellow means low activity, orange medium activity and red high activity.Guidelines on safe browsing
First and foremost, enable automatic updates for your operating system as well your browsers, browser plugins and other applications you are using. Automatic updates ensure that your computer receives the latest security patches as they are published. We also recommend that you run an anti-virus engine that checks network traffic and files on your computer for known malware and abnormal behavior. If you want to be really sure that your system does not become permanently compromised, you might even want to run your browser in a virtual machine, which you can revert to a clean snapshot after every browsing session.
Webmasters can learn more about cleaning, and most importantly, keeping their sites secure at StopBadware.org's Tips for Cleaning and Securing a Website.